Empowering Afghanistan Through Smart IT Solutions
This website is still under development... New features and content are on the way — stay tuned! Thank you for your patience and for stopping by.
Get in TouchWhy Cyber Trust?
Cyber Trust IT Services Company is Afghanistan’s first company to introduce IT Service Packages, making professional IT support affordable and accessible without needing an in-house team. We provide innovative solutions that drive growth and digital transformation.
Our services include Software Development, Network Design, Cybersecurity, Cloud Hosting, and Professional IT Training. We are committed to delivering value and helping businesses succeed in a connected world.

Driving Digital Transformation in Afghanistan
We're committed to empowering businesses and institutions through innovative technology solutions.
Our Mission
To bridge the digital gap by providing affordable, efficient, and secure IT solutions that empower businesses, institutions, and entrepreneurs to leverage the full potential of technology.
Our Vision
To be the most trusted and innovative IT services provider in Afghanistan, delivering high-quality, cost-effective, and technology-driven solutions that help businesses thrive.
Core Values
These principles guide every decision we make and every solution we deliver.
Innovation
We constantly explore new technologies to deliver cutting-edge solutions.
Trust & Integrity
We build long-term relationships through transparency and reliability.
Excellence
We strive for the highest quality in every service we provide.
Customer-Centric Approach
We tailor our solutions to meet the specific needs of our clients.
Continuous Learning
We invest in skills development and innovation to stay ahead of the industry.
Our Services
Comprehensive IT solutions tailored for Afghanistan’s unique business landscape.

Web Development
We design and develop professional websites tailored to your business goals. Whether you're a startup, NGO, or enterpris...
Learn More




Our Products
Pre-built software solutions designed for Afghanistan's market needs.
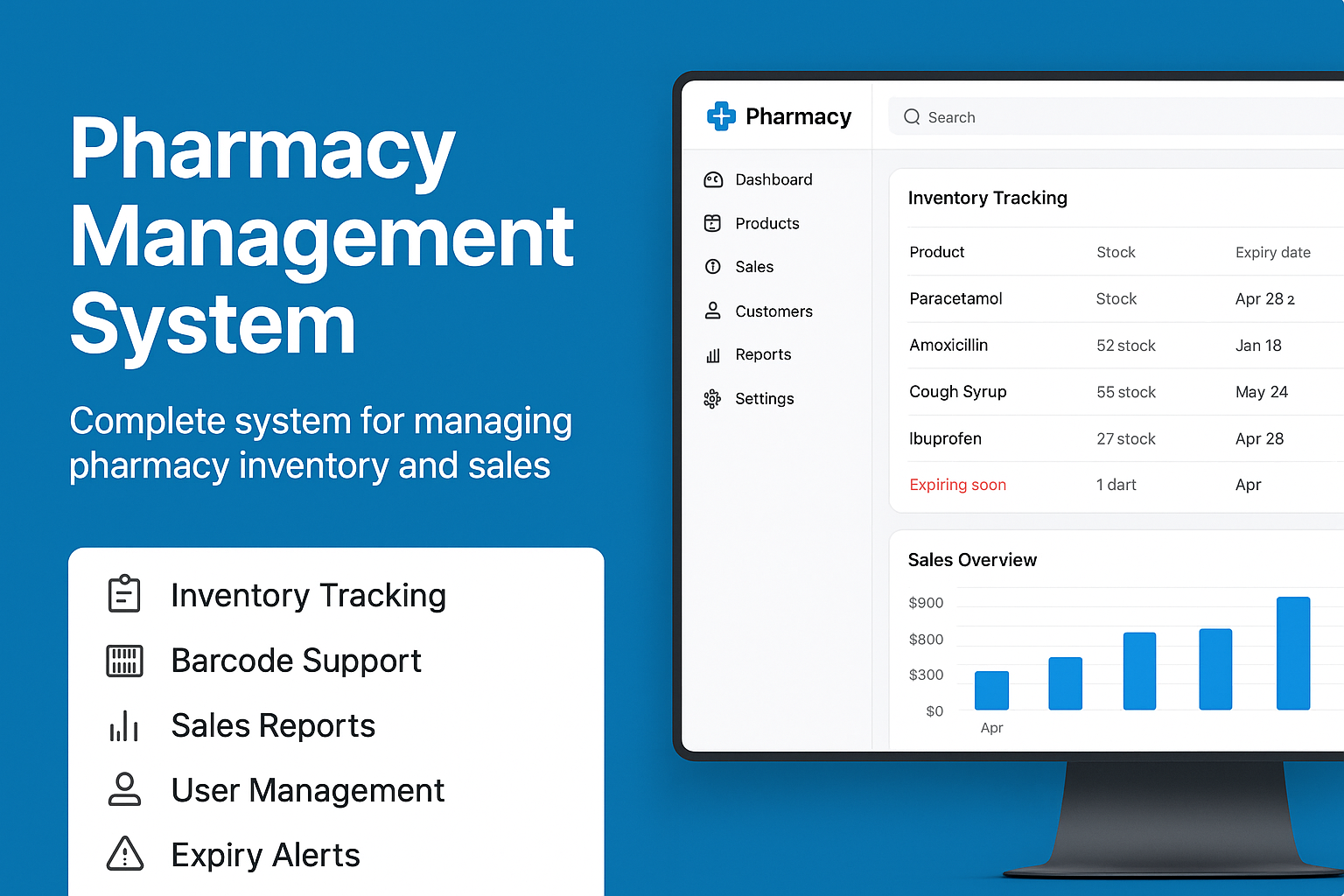
Pharmacy Management System
Complete system for managing pharmacy inventory and sales
- Inventory Tracking
- Barcode Support
- Sales Reports
- User Management
- Expiry Alerts
- Supplier Management

Pharmacy Management System
300$Complete system for managing pharmacy inventory and sales
- Inventory Tracking
- Barcode Support
- Sales Reports
- User Management
- Expiry Alerts
- Supplier Management

Latoon – Lost and Found System
Smart platform for managing lost and found items
- Item Registration
- Document Verification
- Tracking System
- Public Portal
- Admin Dashboard
HMS
$500End-to-end solution for hospital administration
- Patient Records
- Doctor Scheduling
- Billing
- Lab Reports
- Pharmacy Module
- Room Management
Case Studies
See how we've helped organizations across Afghanistan achieve their digital goals.
Luna Electric Web App
We designed and developed a full-featured dynamic website for LUNA Electric Company, a private enter...
View Case Study
Latoon – Lost and Found App
Latoon is a mobile and web-based platform developed to help users register, verify, and track lost a...
View Case Study
HYSIO Baghlan Province Management System
Cyber Trust IT Services successfully developed and deployed the Baghlan Province Management System (...
View Case Study
ESAAR Organization – Hosting & Cloud Services
Delivered secure hosting and cloud infrastructure services, including email setup and server managem...
View Case Study
CAHPO NGO – Network Design & Administration
Full network design and setup for CAHPO NGO including structured cabling, router and switch configur...
View Case Study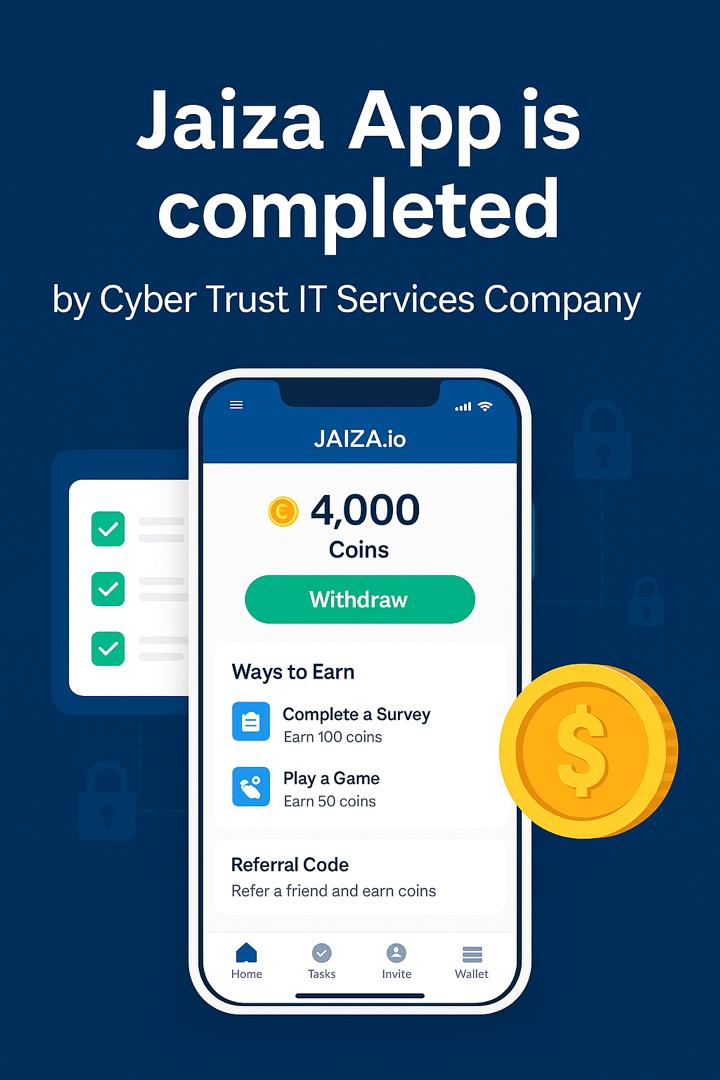
Jaiza – Web-Based Online Earning Platform
Jaiza is a web-based platform developed by CyberTrust to offer secure online earning opportunities s...
View Case StudyMeet Our Leadership
The visionaries driving our company's success and innovation
What Our Clients Say
What Our Clients Say
Latest From Our Blog
Stay updated with the latest trends, news, and insights in Afghanistan's tech landscape.

Top 5 Cybersecurity Practices Every Afghan Business Must Follow
With increasing cyber threats across Afghanistan, small and medium businesses must strengthen their cybersecurity. Disco...
Read ArticleOur Partners
We work with leading organizations to deliver exceptional results.
Trusted Partners

Salam University
Academic
Sheikh Zayed University
Academic
Deeper Network
Technology
Cisco
Technology
Odoo - Open Source ERP
TechnologyReady to Transform Your Business?
Let’s discuss how Cyber Trust can help you achieve your digital goals in Afghanistan.





