Cloud Penetration
Cloud Penetration Testing is the process of detecting and exploiting security vulnerabilities in your cloud infrastructure by simulating a controlled cyber attack. Cloud pentest is performed under strict guidelines from the cloud service providers like AWS, and GCP.
Contact UsWhat are common threats in cloud computing?

Security Vulnerabilities

Data breaches

vulnerability Detection
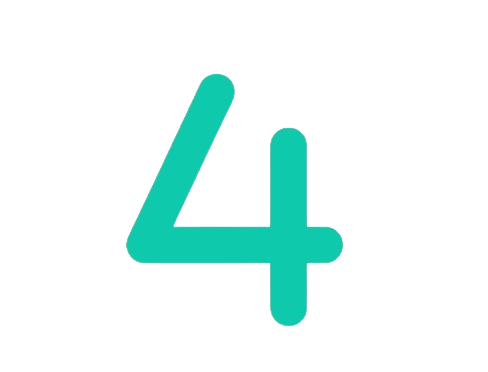
Malware/ransomware

Inappropriate use of cloud services
How can Cyber trust help?
Organizations are moving their application workloads to the cloud to become more agile, reduce time to market, and lower costs. Whether you’re developing a cloud-native application or migrating an existing application to the cloud, Synopses can help you increase innovation, reliability, and efficiency without sacrificing security.